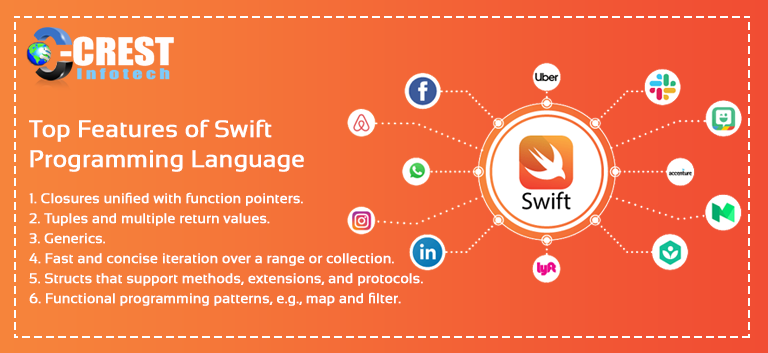
Open Source
Swift applications were created by Swift.org, a website dedicated to the open-source Swift community. It’s built with source code, a bug tracker, mailing lists, and standard development mailing lists.
Swift.org also offers a Linux version of the language, as well as a Linux toolset that includes support for package managers, the LLDB debugger, and the REPLMac. Swift can be used to build applications for iOS Development, OS X, tvOS and watchOS . It does, however, need a Mac to run.
To put it another way, Swift makes application creation safer and quicker while also increasing the enjoyment of programming.
Advancement in Syntax
You can now write more expressive code with Swift’s new syntax tools. New Objective-C features including null-ability and generics descriptions were used in the SDKs to make code safer and cleaner.
Interactive Playgrounds
Professional developers will profit from Swift’s Playgrounds. It helps programmers to experiment with new Graphics or algorithm routines without having to create an entire iPhone application.
Inline code execution has now been introduced to Apple’s playgrounds, allowing programmers to write an algorithm or a large number of codes while receiving input.
This feedback loop has the potential to increase the speed at which code can be written.
In addition to embedded images and links, playgrounds may contain comments that use bullet lists.
Safety
Swift eliminates whole swaths of potentially dangerous code. Integers, for example, are tested for overflow, variables are always initialised before being used, and memory management is done automatically.
Another advantage of Swift is that its objects can never be empty, which means that if you write poor code, it will generate a compiler error. In other words, bugs can be solved as code is written, reducing the amount of time and money spent on error correction.
Finally, if a NIL optional variable is used, it causes a runtime crash, which may help you avoid the bug or repair it faster in Swift code.
Fast and Powerful
Swift has changed dramatically as a result of the removal of legacy C conventions. It converts Swift code into optimised native code using the LLVM compiler, which is extremely fast.
Swift has rendered object categorization much faster and more efficient than Python. In reality, it provides developers with essential object-oriented features including classes, protocols, and generics, giving Cocoa and Cocoa Touch developers the authority and performance they need.
In reality, it provides developers with essential object-oriented features including classes, protocols, and generics, giving Cocoa and Cocoa Touch developers the authority and performance they need.
Objective-C Interoperability
Since Swift is backwards compatible with Objective-C, you can create a project that includes files written in both languages. Apps with a mixed-language codebase can be developed.
You can also use Swift’s new features to incorporate elements of your app’s functionality and seamlessly integrate it back into your current Objective-C codebase.
It Is Built for Safety
Safety is the most important consideration for someone developing an app. The best thing is that when you work with Swift, you won’t have to deal with any potentially dangerous code.
It also employs the most up-to-date programming conventions to assist developers in maintaining the security of the apps they create.
It’s worth noting that in the programming language, valuables can be defined as value types or optional types. It means that a skilled developer has the authority to determine whether or not a value exists (nil).
It means that if a developer chooses Zero as an option, It means that if a developer makes the mistake of using the NIL optional value, the programming language would cause a runtime crash. This stays on the line of code, pushing the developer to fix any bugs as soon as possible.
To summarise, Swift does not allow you to create dangerous bugs or exception-free applications.
If you want cost cutting to your iOS mobile application, you can go for React Native Development or Ionic App Development which support to iOS as well as Android..
You can Hire iOS Developer for part time, full time and scheduled time of period for your business development process. Contact Crest Infotech to know more about iOS Development services in Details.